Since March 18, 2022, two-factor authentication has been deployed for all Sentinel users and is mandatory. This is an additional layer of security that would prevent an attacker with access to your username and password from logging into Sentinel with your identity.
Security Questions
Starting March 18, 2022, all users who have not yet set up their security questions will be directed to a setup page upon first login. You will be asked to choose three security questions and provide an answer to each.
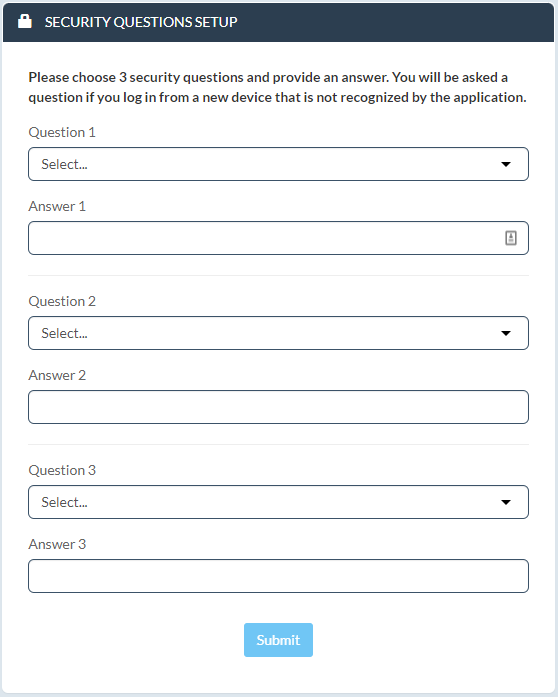
Once the questions are set up, you will be asked one of three questions at random when you log in, if any of the following conditions are met:
- You are logging on to a device for the first time or you have cleared your cookies on the browser of this device.
- A week has passed since you were asked a security question on this device.
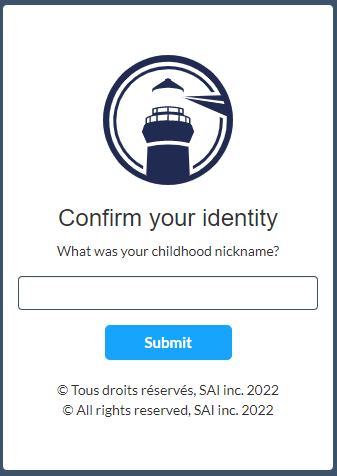
You have 5 attempts to answer the security question you are asked. If the answer entered is still not valid after 5 attempts, the account will be locked and you will not be able to make additional login attempts. In such a case, you have two options:
- You can reset your password yourself by clicking on the “Forgot your password?” link on the login screen. You will receive a link by email to reset your password and you can try again to answer the security question.
- Alternatively, you can contact an administrator of your organization to ask them to unlock your account or, in addition, to reset your security questions and/or your password.
For Administrators
If you are a Sentinel administrator of your organization, you will find 3 buttons in the profiles of your users which allow you to manage their login:
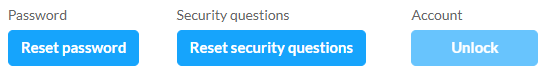
- Reset password: The user will receive a link to their email address to update their password. This also has the effect of unlocking the account, i.e. resetting connection attempts with wrong passwords or security answers.
- Reset questions: The user will need to reset their security questions the next time they log in before being able to access Sentinel. This also has the effect of unlocking the account, i.e. resetting connection attempts with wrong passwords or security answers.
- Unlock account: Resets wrong password or security answer login attempts to 0, without resetting the password or security questions.

Comments
0 comments
Article is closed for comments.